Configuring the webhook service for audit data
The Kyndryl Cloud Uplift webhook service provides Kyndryl Cloud Uplift account audit data in real time to a URL that you choose. Because the data is streamed continuously, you don’t need to query Kyndryl Cloud Uplift for updated information.
The auditing webhook service provides account-wide auditing data—exactly the same data available from the administrator Auditing page—in a real-time, continuous data stream.
Use the webhook service to create custom applications and reports. For example, if your organization uses scripts or other automation to add and remove VMs to a DNS server or Active Directory Domain server, the auditing webhook can provide environment data that the scripts can consume to automate these tasks.
To configure the auditing webhook
-
Click Manage > Settings to navigate to the Settings page.
-
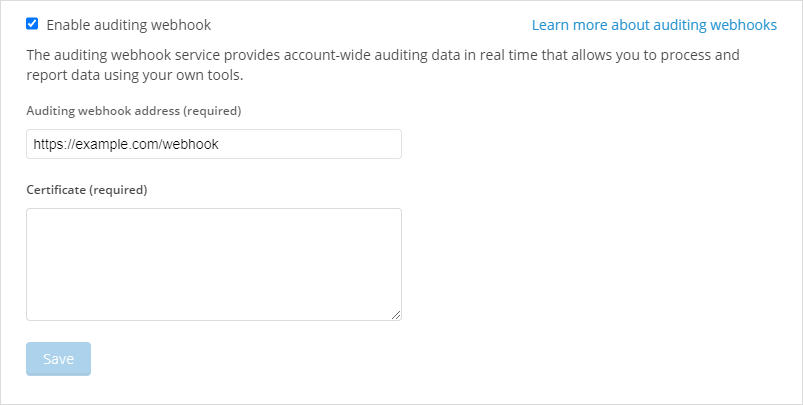
Under Auditing Webhook, click Enable webhook. The Auditing Webhook section expands.
-
Type the Webhook URL where the data will be sent. All audit events for the account will be sent to the destination URL.
The Webhook URL must use HTTPS over port 443.
-
Type or paste the public TLS Certificate for the destination site.
You can use OpenSSL to retrieve the TLS public key with the following command:
openssl s_client -showcerts -connect {webhookserver}:{port} </dev/null 2>/dev/null|openssl x509 -outform PEM
-
Click Save webhook.
If the destination URL isn’t available or stops responding, the webhook service will attempt to reconnect once per minute for up to six hours or 200 attempts. If it can’t reconnect, the webhook service will be disabled until you reconfigure it.
Kyndryl Cloud Uplift webhook data format
The webhook generates a JSON representation of all of the data available from the administrator Auditing report. For a complete list of auditing activities, see Generating audit reports
Example Kyndryl Cloud Uplift webhook data payload
{
"version": 1,
"message_id": "456",
"category": "auditing",
"timestamp": "2000-01-01T00:00:00Z",
"Payload": [{
"id": 98765432,
"type": "Shutdown Environment",
"type_code": "ShutdownConfigurationHistory",
"date": "2019-01-27T12:34:56Z",
"region": "us-west",
"payload": {},
"user": {"id": null, "name": "auto_power_options"},
"department": {"id": null, "name": null},
"project": {"id": null, "name": null},
"operation_id": "trn.a1b2c3456d78987654ef3edc210b1234.56789.876/trn.5a5432b10c1d234567ef8e9d8cb7654a.3210.123.4",
"customer": {"id": "666", "name": "Administrators"},
"operated_on": [
{"resource_type": "environment", "name": "Copy of ubuntu - diskless", "id": 9876543, "guid": "configuration-1234567"},
{"resource_type": "vm", "name": "Ubuntu 10.04 desktop", "id": 2832140, "guid": "vm-1234567-8987654"}
]
}]
}
