VPN configuration parameters
This article supplements the instructions in Creating a VPN.
Contents
VPN configuration options
The following table describes the Kyndryl Cloud Uplift VPN parameters.
Notes
Most of the Kyndryl Cloud Uplift VPN configuration values are determined by your IT organization, based on the VPN endpoint device that Kyndryl Cloud Uplift is connecting to.
Work closely with your IT organization ensure that the following values match exactly on both the VPN endpoint device and the Kyndryl Cloud Uplift VPN configuration page:
Topology (route-based or policy-based)Phase 1 encryption algorithmPhase 1 hash algorithmPhase 1 pre-shared keyPhase 1 SA lifetimePhase 1 DH groupPhase 2 encryption algorithmPhase 2 authentication algorithmPhase 2 PFSPhase 2 PFS groupPhase 2 SA lifetimePhase 2 Dead Peer DetectionIKE protocol version
If these parameters don't match exactly on the Kyndryl Cloud Uplift and VPN endpoint configurations, the VPN will experience immediate and intermittent errors.
The one parameter generated by Kyndryl Cloud Uplift—the Kyndryl Cloud Uplift peer IP—must be supplied to your IT group so that it can be configured on the remote end of the tunnel.
For links to detailed information about configuring your Kyndryl Cloud Uplift VPN to connect with common VPN endpoints (such as Cisco ASA, Cisco IOS, and Juniper SRX), see VPN configuration examples below.
Parameter Name
Description
Where Does the Value Come From?
Example
Name
Enter a name for the Kyndryl Cloud Uplift VPN.
Max. 255 characters.
Admin
CorporateVPN
Remote peer IP
Enter the public IP address for the remote VPN endpoint device. The remote VPN endpoint device is typically a network device on your corporate network that has been configured to connect to the Kyndryl Cloud Uplift VPN.
If your VPN device is behind a NAT router, you may need to enable NAT-T (NAT traversal) on the VPN endpoint device to ensure correct address translation.
Customer IT
74.2.147.3
Region
Select an available region in your account.
This field is related to Kyndryl Cloud Uplift peer IP below. You must select a static public IP address in the same region as the Kyndryl Cloud Uplift VPN.
US-West
Kyndryl Cloud Uplift peer IP
Select an available static public IP address in your Kyndryl Cloud Uplift account.
This IP address is used exclusively by the Kyndryl Cloud Uplift VPN. When a Kyndryl Cloud Uplift static public IP is used by a VPN, it isn’t available for use by VMs in Kyndryl Cloud Uplift.
Selected from available public IP addresses listed on the VPNs page, or allocated as needed from the under the Manage > Public IP tab
76.32.14.101
Kyndryl Cloud Uplift subnet
Enter the subnet for the VMs in Kyndryl Cloud Uplift that will send and receive traffic through this VPN.
Notes
- Traffic sent to the Kyndryl Cloud Uplift subnet (destination) from included subnets on the external network (source) are routed through the IPsec tunnel.
- Traffic sent to the external network (destination) from IP addresses in the Kyndryl Cloud Uplift subnet (source) are routed through the IPsec tunnel as defined by the internal and external remote subnets rules (see below).
- This subnet can't overlap with restricted subnets or included remote subnets (defined below).
When NAT is enabled on the VPN (see below), NAT IP addresses are allocated from this subnet.
Customer IT
10.1.0.0/23
Select whether to enable NAT for Kyndryl Cloud Uplift virtual networks connected to the VPN.
Options: YES or NO.
If YES, the VPN assigns unique NAT IP addresses to all VMs connected to the VPN. Traffic between the VPN and the VMs occurs over these NAT IP addresses.
NAT automatically assigns IP addresses from the Kyndryl Cloud Uplift subnet defined above.
The Kyndryl Cloud Uplift subnet should be large enough to accommodate all of the VMs that will be attached to the VPN. Allow for future growth with additional VMs. We recommend a /22 subnet or larger. It is easier to set a large subnet during the initial VPN configuration than to extend the NAT subnet after NAT IP addresses have been assigned.
Notes
- If your VPN device is behind a NAT router, you may need to enable NAT-T (NAT traversal) on your VPN endpoint device to ensure correct address translation.
- For more information, see Using Network Address Translation (NAT) to avoid IP address conflicts.
Admin
YES
Select the topology that matches the remote VPN endpoint.
Options:
- Policy-based: With policy-based VPNs, access to the VPN is determined by IPsec policy (most commonly used).
- Route-based: Route-based VPNs use static or dynamic IP routes and ACLs to direct the traffic to its desired endpoint.
Customer IT
Policy-based
Select the algorithm for Phase 1 encryption.
Options: aes or aes 256
We strongly recommend aes 256.
Customer IT
aes 256
Select the hash algorithm for Phase 1 authentication.
Options: sha1 or sha256
We strongly recommend sha256.
Customer IT
sha256
Enter the Phase 1 pre-shared key. This is a text string up to 128 characters, used to validate endpoints before protocol negotiation.
Notes
- The current value of the key isn't displayed to any user. The key can only be updated to a new value using the Edit VPN link.
- The key should meet the following complexity requirements:
- Be different from previous pre-shared keys.
- Have at least 12 characters.
- Contain least 3 of each of the following:
- Lowercase letters.
- Uppercase letters.
- Numbers.
- Special characters (except double-quote characters ("), which aren't supported).
- Additionally, the key should not contain dictionary words, repeated characters ('bbb'), or sequential characters ('1234').
Customer IT
sc3c4SIWitPlSuP1
luNnP88gpM+FjH2g
pDdYkT30RDN10xFN
hEO9Gp2IXTG7m+NJ
Enter a value (in seconds) for the Phase 1 Security Association (SA) lifetime.
Valid range: 1 to 2147483647.
Customer IT
28800
Select the Diffie-Hellman (DH) group for Phase 1.
Options: modp1536 (5) or modp2048 (14)
We strongly recommend modp2048 (14).
Customer IT
modp2048 (14)
Select the algorithm for Phase 2 encryption.
Options: aes, aes 256, or aes_gcm
aes_gcm generally provides the highest connection throughput.
Customer IT
aes_gcm
Select the algorithm for Phase 2 authentication.
Options: hmac_sha1 or hmac_sha256
We strongly recommend hmac_sha256.
Customer IT
hmac_sha256
Select whether to enable Perfect Forward Secrecy (PFS).
Options: ON or OFF
We strongly recommend ON.
Customer IT
ON
If Phase 2 PFS is enabled (above), select the Diffie-Hellman group to use.
Options: modp1536 (5) or modp2048 (14)
We strongly recommend modp2048 (14).
Customer IT
modp2048 (14)
Value (in seconds) for the Phase 2 Security Association (SA) lifetime.
Valid range: 1 to 2147483647.
Customer IT
3600
SA policy level
Select the Security Association (SA) Policy Level for policy-based VPNs.
Options: require or unique
On route-based VPNs, this field is disabled.
Customer IT
require
Specify maximum segment size
Select whether to enable a non-standard maximum segment size (below).
Generally, this should be used only if it’s required by the remote VPN endpoint, or to troubleshoot VPN errors.
Options: YES or NO
For VPN endpoints hosted in Microsoft Azure regions (except US-Virginia-M-1), choose YES.
Customer IT
NO
Maximum segment size
If Specify maximum segment size is enabled (above), enter the non-standard maximum segment size.
Valid range: 536 to 1460.
For VPN endpoints hosted in Microsoft Azure regions (except US-Virginia-M-1), choose 1200 or lower.
Customer IT
1200
Remote Subnets options
After you create a VPN, you must define at least one remote subnet to include. You can also choose remote subnets to exclude.
You must include at least one remote subnet or the VPN won’t work.
Parameter Name
Description
Where Does the Value Come From?
Example
include
(required)
IP addresses and subnets on the external network that send and receive traffic through this VPN.
- You can specify the default route (0.0.0.0/0) for either the remote subnet or the local subnet. You can’t use 0.0.0.0/0 for both local and remote subnets.
- Traffic sent to included remote subnets (destination) from the Kyndryl Cloud Uplift subnet (source) is routed through the IPsec tunnel.
- This subnet can’t overlap with restricted subnets or the Kyndryl Cloud Uplift subnet (defined above).
IKEv2, policy-based VPNs are limited to 32 remote subnets.
Customer IT
192.168.0.0/24, 172.16.0.0/24
exclude
(optional)
Subset of IP addresses and subnets on the external network that should be excluded from using the VPN tunnel. This is only used to define exclusions for VPN traffic from larger included remote subnets.
- Each excluded remote subnet must be contained by an included remote subnet. For example, if an included remote subnet is
192.0.0.0/24, you can exclude the remote subnet192.0.0.0/28. - Traffic from the Kyndryl Cloud Uplift subnet to an excluded remote subnet bypasses the VPN tunnel and goes directly to the public Internet.
This is “bypass” security policy; the VPN router continues to manage these routes.
Customer IT
192.168.0.240/28
IKE protocol support
Kyndryl Cloud Uplift VPNs support the IKEv1 and IKEv2 protocols.
IKEv2, policy-based VPNs are limited to 32 remote subnets.
VPN configuration examples for common devices and endpoints
- AWS VPC: VPN configuration example
- Azure VPN: VPN configuration example
- Cisco ASA: VPN configuration example
- Cisco IOS: VPN configuration example
- Juniper SRX: VPN configuration example
- pfSense: VPN configuration example
- strongSwan: VPN configuration example
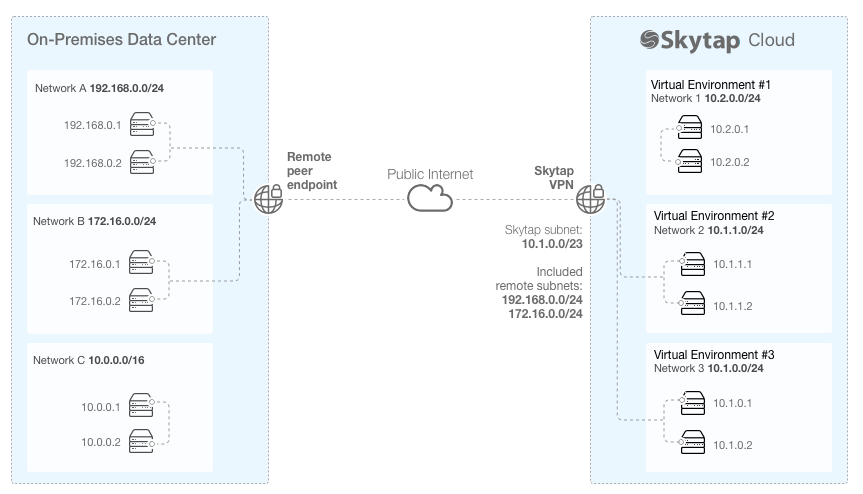
Sample VPN diagram
This simplified diagram shows Kyndryl Cloud Uplift VMs in the 10.1.0.0/23 IP address range communicating with external machines in the 192.168.0.0/24 and 172.16.0.0/24 IP address range. This diagram doesn’t illustrate any excluded remote subnets.