Using Network Address Translation (NAT) to avoid IP address conflicts
Network address translation (NAT) is a networking feature that helps you connect environments that have overlapping IP addresses. NAT prevents IP address conflicts by mapping a unique IP address to every VM on a connected network. This NAT IP address is used for inbound and outbound communication with the NAT-enabled network.
Contents
NAT overview
By default, each Kyndryl Cloud Uplift environment has a private network that is isolated from other Kyndryl Cloud Uplift environment networks. This isolation lets you run multiple environments with the same network subnet at the same time.
Occasionally, you may need to connect multiple environments together using ICNR (for example, to communicate across VMs or share resources between multiple environments). Rather than manually change the subnet of each environment to avoid IP address conflicts, you can enable NAT to automatically assign unique IP addresses to connected VMs. NAT can also be enabled on a Kyndryl Cloud Uplift VPN, allowing identical Kyndryl Cloud Uplift environments to connect back to your corporate network.
How it works
When NAT is enabled on a network, a NAT IP address is automatically assigned to each VM on a connected network.
For example, if NAT is enabled on Network A and then Network A is connected to Network B, NAT IP addresses are assigned to the VMs connected to Network B. When Network A and B communicate, the VMs in Network B use the NAT IP addresses to send and receive traffic.
Network A automatically assigns NAT IP addresses from the NAT subnet defined in its network settings.
NAT examples
Three networks, two with overlapping IP addresses (ICNR)
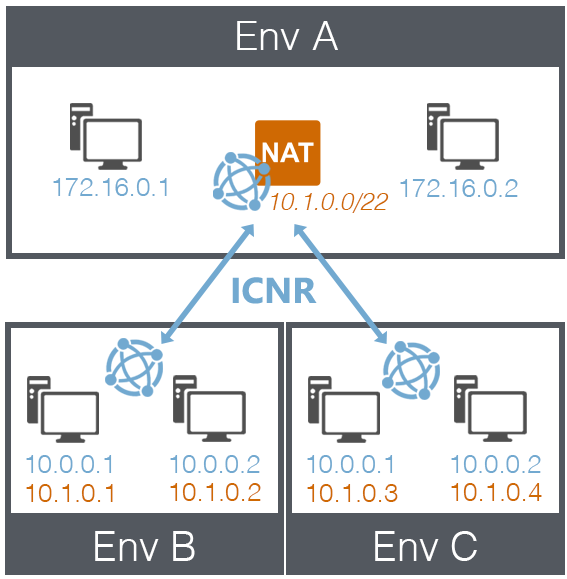
Environment A
- Shared resource environment
-
NAT-enabled network
- Network subnet: 172.16.0.0/12
- NAT subnet 10.1.0.0/22
Environment B
- Network subnet: 10.0.0.0/22
- Network in Environment B is connected to network in Environment A (via ICNR)
- VMs in Environment B receive NAT IP addresses from Environment A
Environment C
- Network subnet: 10.0.0.0/22
- Network in Environment C is connected to network in Environment A (via ICNR)
- VMs in Environment C receive NAT IP addresses from Environment A
Two networks with overlapping IP addresses (ICNR)
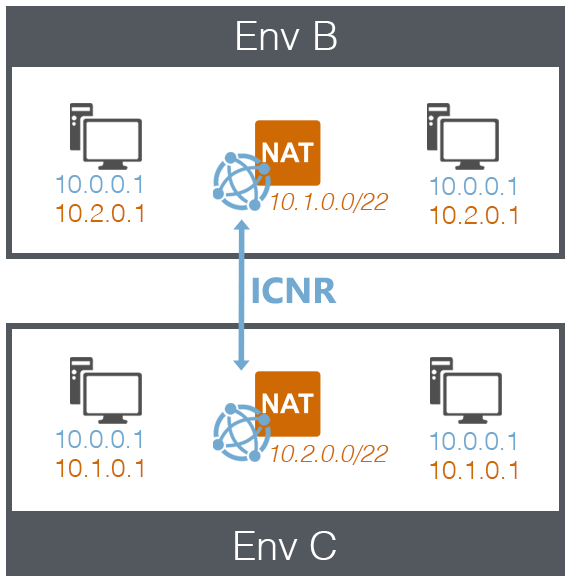
Environment B
-
NAT-enabled network
- Network subnet: 10.0.0.0/22
- NAT subnet 10.1.0.0/22
- Network in Environment B is connected to network in Environment C (via ICNR)
- VMs in Environment B receive NAT IP addresses from Environment C
Environment C
-
NAT-enabled network
- Network subnet: 10.0.0.0/22
- NAT subnet 10.2.0.0/22
-
VMs in Environment C receive NAT IP addresses from Environment B
VPN connection with two environments that have overlapping IP addresses
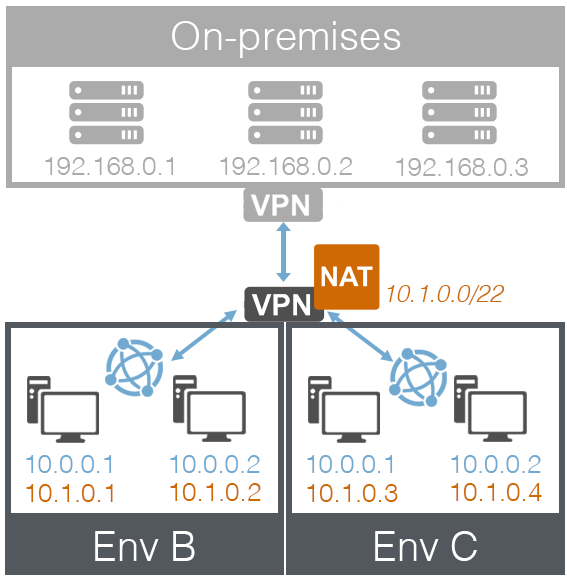
On-premises environment
- Connected to Kyndryl Cloud Uplift via NAT-enabled VPN connection
- The Kyndryl Cloud Uplift subnet on the VPN is 10.1.0.0/22; this doubles as the NAT IP subnet.
Environment B
- Network subnet: 10.0.0.0/22
- Network in Environment B is attached to VPN
- VMs in Environment B receive NAT IP addresses from VPN
Environment C
- Network subnet: 10.0.0.0/22
- Network in Environment C is attached to VPN
- VMs in Environment C receive NAT IP addresses from VPN
NAT IP address management
When NAT is enabled on a network or a Kyndryl Cloud Uplift VPN, a NAT IP address is automatically assigned to each VM on a connected network. The NAT IP addresses are allocated to VMs from the NAT subnet. The NAT subnet is defined the network settings (for NAT-enabled networks) or the VPN settings (for NAT-enabled VPNs).
To avoid running out of NAT IP addresses, set the NAT subnet size so it’s large enough to handle multiple NAT connections. We recommend a /22 subnet or larger. It is easier to set a large subnet during the initial network or VPN configuration than to extend the NAT subnet after NAT IP addresses have been assigned.
The NAT IP address given to a VM depends on:
- The size of the network or the NAT subnet for the VPN.
- The IP addresses that are already distributed and assigned.
The VM NAT IP address remains static through all VM state changes (run, suspend, and shutdown). The VM NAT IP address assignment remains static until:
- The VM is disconnected from the network that is connected to the NAT-enabled network, or VPN.
- The environment network is disconnected from the NAT-enabled network or WAN.
Enabling NAT on an environment network or Kyndryl Cloud Uplift VPN
- To enable NAT on an environment network, click Apply NAT for connecting networks in the network settings. For detailed instructions, see Editing an automatic network.
- To enable NAT on a Kyndryl Cloud Uplift VPN, select Apply NAT for connecting networks in the VPN settings. For detailed instructions, see Creating a VPN connection.
Locating a VM NAT IP address
To locate the IP addresses associated with a VM, including any NAT IP addresses, see Finding the IP addresses for a VM.
Troubleshooting
Error: The operation failed because there are no IP addresses remaining in the NAT pool of one of the networks.
After the NAT subnet has used all of its IP addresses, you can’t:
- Add VMs or network adapters to a network that is connected to the NAT-enabled Kyndryl Cloud Uplift VPN or to a NAT-enabled network.
- Connect any additional networks to the NAT-enabled VPN or NAT-enabled network.
Resolution
To create additional NAT IP addresses, you must:
-
Disconnect a network from the NAT-enabled network.
or
-
Disconnect VMs from the networks that are connected to a NAT-enabled network or to a VPN.
or
-
Expand the subnet by disconnecting all networks, modifying the NAT subnet, and then reestablishing network connections.
- To edit the NAT subnet for a network, edit the network settings.
- To edit the NAT subnet for a Kyndryl Cloud Uplift VPN, edit the Kyndryl Cloud Uplift subnet setting in the Kyndryl Cloud Uplift VPN.
