Accessing VMs with published services
Contents
Published services overview
A published service exposes a port on your VM to the public Internet via port forwarding. The exposed port permits both TCP and UDP traffic between services running on the VM and the public Internet.
Published service access may be disabled by your administrator.
Published services are commonly used to access a VM via SSH or direct RDP, or to access web or application services running on a VM.
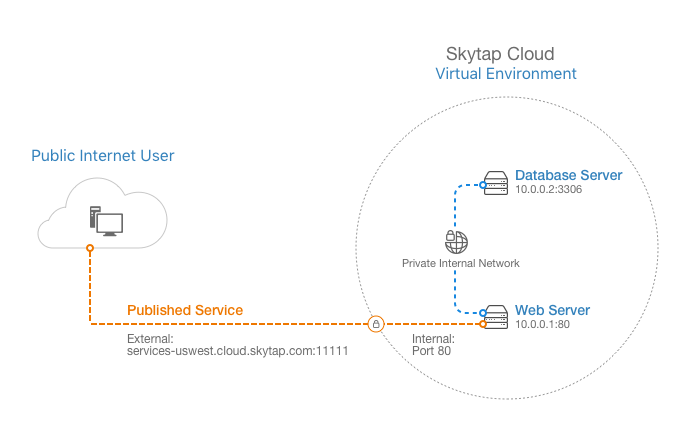
When you add a published service to a VM
- You define the port you want to open on the VM (for example, port 3389 for direct RDP, port 22 for SSH, or port 80 for web services). You specify a port number or select from commonly-used ports.
- Kyndryl Cloud Uplift automatically assigns a public address and random external port number for the published service (for example,
services-apac.cloud.skytap.com:12345). When you access the VM via the published service, traffic is forwarded from the published service port (for example, 12345) to the VM port you defined (for example, 3389). The full range of ports used by published services is 8193 – 32767 (inclusive). - Kyndryl Cloud Uplift doesn’t create or start services on the VM. You must configure the VM guest operating system and applications running on the VM to accept the remote connection.
Because a published service exposes a port to the public internet, we strongly recommend that you review Exposing and blocking public Internet access to VMs and Protecting a VM that is exposed to the internet or compromised.
Select protocols don't work with published services, including:
- FTP and other protocols that make secondary connections on different port numbers.
- Protocols that don't work behind a Network Address Translation or Port Address Translation (NAT/PAT) gateway.
How to create and use published services
For detailed instructions, see the following topics:
- Adding a published service
- Connecting to a published service
- Troubleshooting a published service
- Removing a published service
For more specific guidance about using published services to connect to a VM over RDP or SSH, see:
Accessing an open port on a VM that has a public IP address, or that uses a VPN
A published service may not be needed to access a port on the VM from the public IP internet or from a VPN:
-
If a VM has an attached public IP address, all of the VM ports are already open to the public Internet. You don’t need to create a separate published service.
Access the open port using the public IP address:
<public-ip-address>:<port-number>(for example: 128.128.128.128:3389)
-
If a VM has a VPN, all of VM ports are already accessible over the VPN connection.
Access the open port over the VM NAT or private IP address:
<vm-nat-ip-address>:<port-number>(for example: 10.0.0.1:3389)
You don’t need to create a separate published service, unless you want to expose the port opening to the public Internet (which is strongly discouraged because of the increased security risks).
Related articles
- For information about other VM access methods, see Accessing VMs.
- For information about the IP addresses and port ranges used by published services, see What IP addresses and port ranges does Kyndryl Cloud Uplift use?
