Controlling public Internet access to VMs
Contents
Overview of default settings
By default, Kyndryl Cloud Uplift virtual networks have the following settings:
| Access type | Status |
|---|---|
| Outbound access to the public Internet (egress) | Enabled for Kyndryl Cloud Uplift customer accounts. This means that virtual machine can access the public Internet. To disable this, see Controlling outbound Internet access. |
| Inbound access from the public Internet (ingress) | Disabled for VMs in all accounts. This means that you can't access the virtual machine from the public Internet. To enable inbound access, see Controlling inbound Internet access. |
Controlling inbound Internet access
- Enabling inbound access to a VM or environment from the public Internet
- Disabling inbound access to a VM or environment from the public Internet
Enabling inbound access to a VM or environment from the public Internet
There are several options for enabling ingress access to a VM or environment from the public Internet.
Some or all of these options may have been disabled for your account.
| Access method | Description |
|---|---|
| Sharing portal | Gives browser-based, remote access to the VM (or multiple VMs in the same environment) via HTTPS port 443 on cloud.skytap.com. The sharing portal can be password-protected and customized to restrict access based on permissions or time limits. The VM ports aren’t directly exposed to the public Internet. For more information, see Sharing VMs and environments with sharing portals. |
| Published service | Opens a single port on the VM, allowing direct inbound and outbound access for a specific protocol (for example, RDP or SSH) over the public Internet. For more information, see Accessing VMs with published services. |
| Public IP address | Exposes all network ports on the VM, allowing direct inbound and outbound access from the public Internet. There are two public IP address options:
|
Published services and public IP addresses require an automatic network to work. If an environment you want to expose is controlled by a manual network, you’ll need to add an automatic network to the environment and additional network adapters connected to the new network. For more information, see Using multiple networks in an environment.
Inbound UDP traffic is blocked over TCP ports 389.
Exposing your environment to the public Internet makes your VMs less secure. Please see Protecting a VM that is exposed to the internet or compromised article for information on best practices.
Disabling inbound access to a VM or environment from the public Internet
To disable inbound access to a VM or environment from the public Internet, remove any:
Controlling outbound Internet access
- Blocking outbound access to the public Internet from VMs in an environment
- Enabling outbound access to the public Internet from VMs in an environment
Blocking outbound access to the public Internet from VMs in an environment
-
Navigate to the Environment page.
-
From the navigation bar, click Environments. Click the Environments tab.
- (Optional) Narrow or sort the list of environments using the filter, search, or sort options.
-
Click the name of the environment.
The Environment Details page displays.
-
- Make sure that VMs are suspended or powered off.
- Click Networking: Settings. The Network Settings page displays.
-
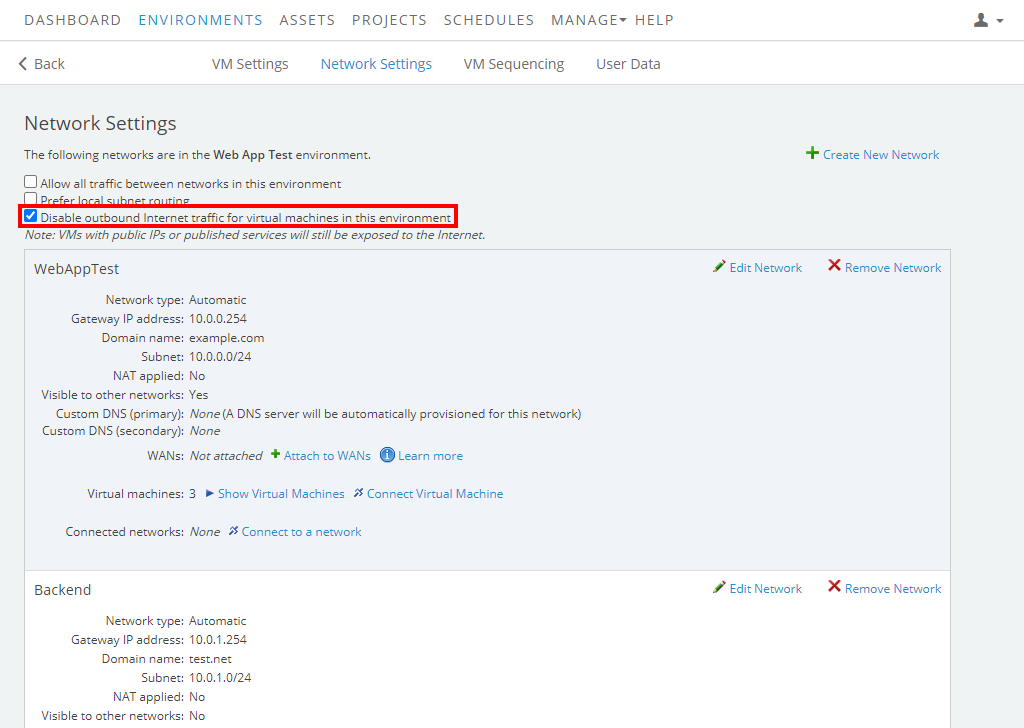
Select Disable outbound Internet traffic for virtual machines in this environment.
Notes
- A VM with a public IP address or published service can still establish an inbound connection from a remote client via the internet (Enabling inbound access to a VM or environment from the public Internet).
- If the network is connected to a VPN or Private Network Connection, outbound connections are permitted over that network. Check with your network administrator if you need to adjust your VPN or Private Network Connection settings.
To enable outbound Internet access for the VMs in an environment
-
Navigate to the Environment page.
-
From the navigation bar, click Environments. Click the Environments tab.

- (Optional) Narrow or sort the list of environments using the filter, search, or sort options.
-
Click the name of the environment.
The Environment Details page displays.

-
- Make sure that VMs are suspended or powered off.
- Click Networking: Settings. The Network Settings page displays.

-
Clear the Disable outbound Internet traffic for virtual machines in this environment checkbox.

Notes
- Outbound SMB traffic is blocked over TCP ports 137, 139, and 445.
- If you can't access the public Internet from a VM after changing this setting, see Issue: I can't access the Internet from my VM.
